Security Services > Intrusion Prevention Service
736
SonicOS Enhanced 4.0 Administrator Guide
How SonicWALL’s Deep Packet Inspection Works
Deep Packet Inspection technology enables the firewall to investigate farther into the protocol
to examine information at the application layer and defend against attacks targeting application
vulnerabilities. This is the technology behind SonicWALL Intrusion Prevention Service.
SonicWALL’s Deep Packet Inspection technology enables dynamic signature updates pushed
from the SonicWALL Distributed Enforcement Architecture.
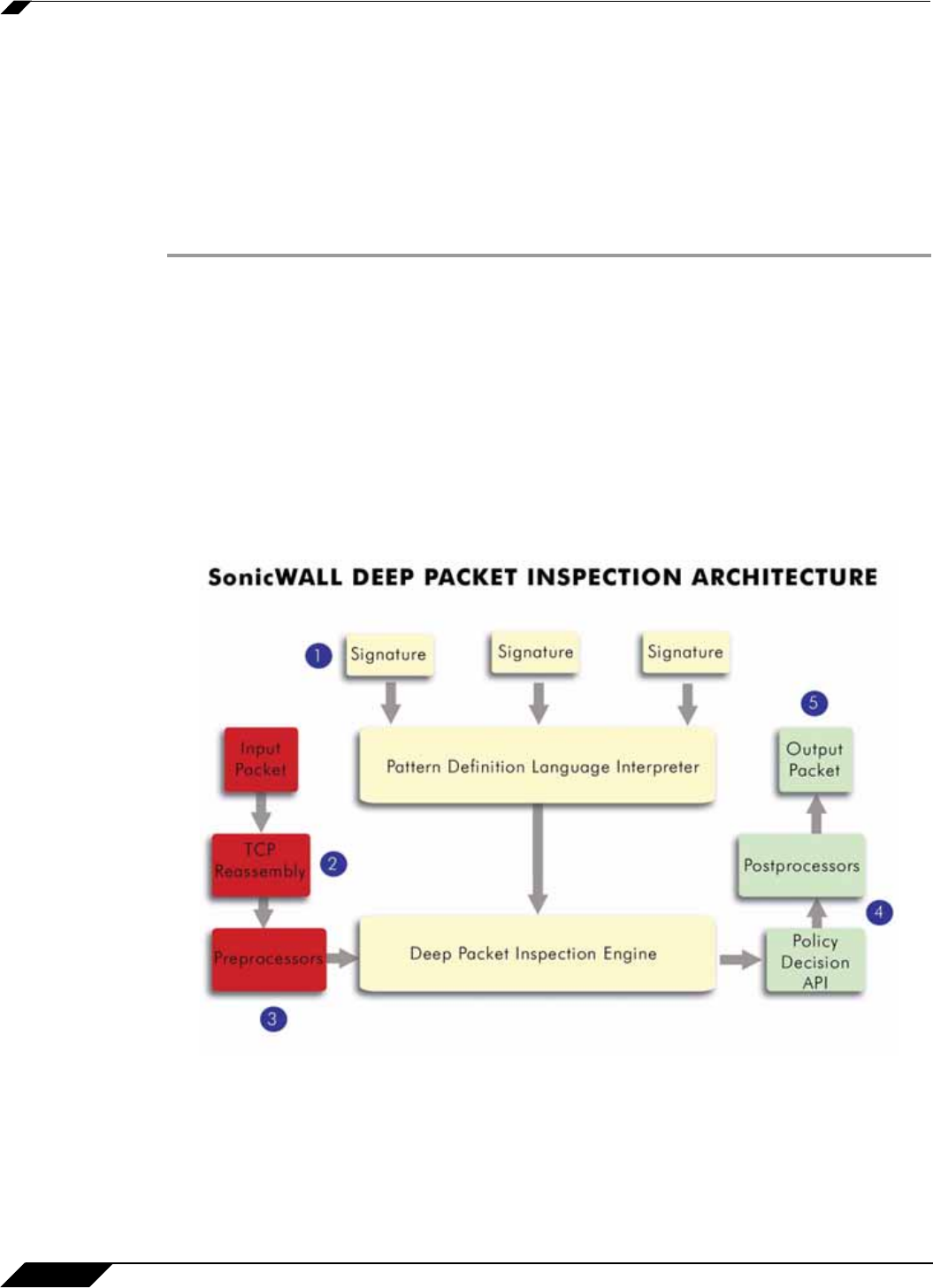
The following steps describe how the SonicWALL Deep Packet Inspection Architecture works:
Step 1 Pattern Definition Language Interpreter uses signatures that can be written to detect and
prevent against known and unknown protocols, applications and exploits.
Step 2 TCP packets arriving out-of-order are reassembled by the Deep Packet Inspection framework.
Step 3 Deep Packet Inspection engine preprocessing involves normalization of the packet’s payload.
For example, a HTTP request may be URL encoded and thus the request is URL decoded in
order to perform correct pattern matching on the payload.
Step 4 Deep Packet Inspection engine postprocessors perform actions which may either simply pass
the packet without modification, or could drop a packet or could even reset a TCP connection.
Step 5 SonicWALL’s Deep Packet Inspection framework supports complete signature matching across
the TCP fragments without performing any reassembly (unless the packets are out of order).
This results in more efficient use of processor and memory for greater performance.
SonicWALL IPS Terminology
• Stateful Packet Inspection - looking at the header of the packet to control access based
on port, protocol, and IP address.


















