Network > Address Objects
216
SonicOS Enhanced 4.0 Administrator Guide
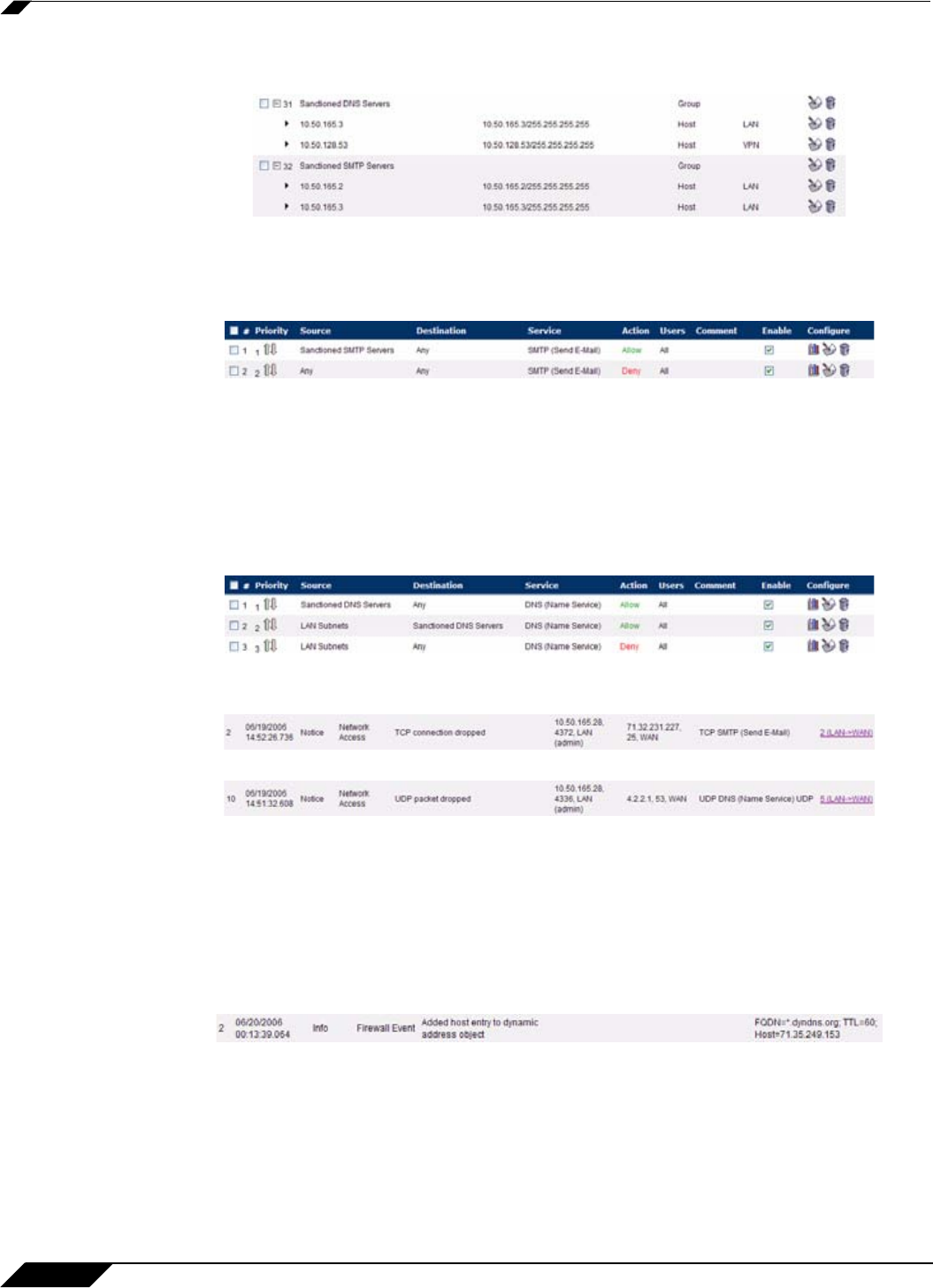
• Create Address Object Groups of sanctioned servers (e.g. SMTP, DNS, etc.)
• Create Access Rules in the relevant Zones allowing only authorized SMTP servers on your
network to communicate outbound SMTP; block all other outbound SMTP traffic to prevent
intentional or unintentional outbound spamming.
• Create Access Rules in the relevant Zones allowing authorized DNS servers on your
network to communicate with all destination hosts using DNS protocols (TCP/UDP 53). Be
sure to have this rule in place if you have DNS servers on your network, and you will be
configuring the restrictive DNS rule that follows.
• Create Access Rules in the relevant Zones allowing Firewalled Hosts to only communicate
DNS (TCP/UDP 53) with sanctioned DNS servers; block all other DNS access to prevent
communications with unauthorized DNS servers.
• Unsanctioned access attempts will then be viewable in the logs.
Using MAC and FQDN Dynamic Address Objects
MAC and FQDN DAOs provide extensive Access Rule construction flexibility. MAC and FQDN
AOs are configured in the same fashion as static Address Objects, that is from the Network >
Address Objects page. Once created, their status can be viewed by a mouse-over of their
appearance, and log events will record their addition and deletion.
Dynamic Address Objects lend themselves to many applications. The following are just a few
examples of how they may be used. Future versions of SonicOS Enhanced may expand their
versatility even further.


















