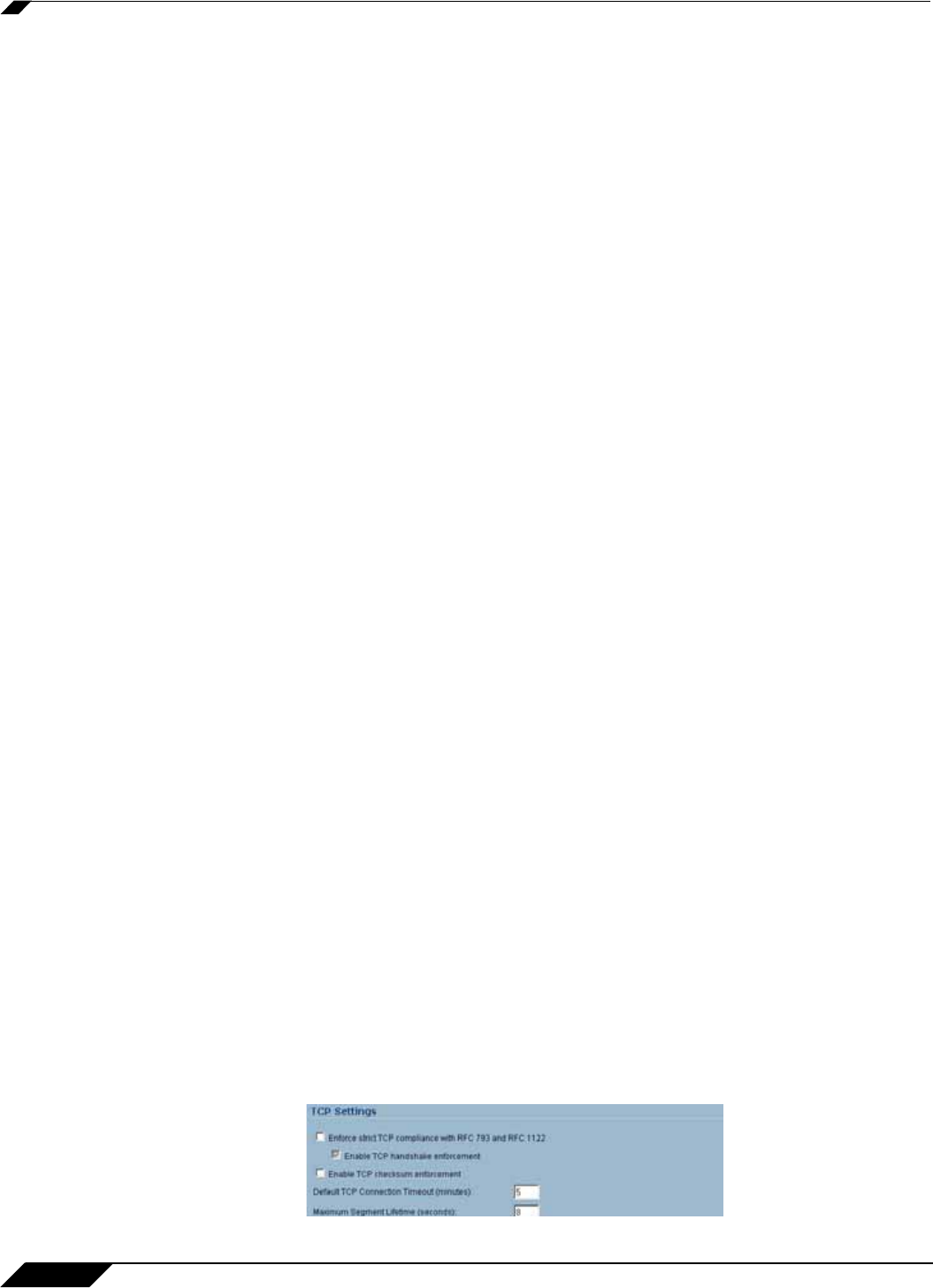
Firewall > TCP Settings
438
SonicOS Enhanced 4.0 Administrator Guide
–
When the TCP SACK Permitted (Selective Acknowledgement, see RFC1072) option is
encountered, but the calculated option length is incorrect.
–
When the TCP MSS (Maximum Segment Size) option is encountered, but the
calculated option length is incorrect.
–
When the TCP SACK option data is calculated to be either less than the minimum of 6
bytes, or modulo incongruent to the block size of 4 bytes.
–
When the TCP option length is determined to be invalid.
–
When the TCP header length is calculated to be less than the minimum of 20 bytes.
–
When the TCP header length is calculated to be greater than the packet’s data length.
• Invalid Flag Packets Dropped - Incremented under the following conditions:
–
When a non-SYN packet is received that cannot be located in the connection-cache
(while SYN Flood protection is disabled).
–
When a packet with flags other than SYN, RST+ACK or SYN+ACK is received during
session establishment (while SYN Flood protection is enabled).
• TCP XMAS Scan will be logged if the packet has FIN, URG, and PSH flags set.
• TCP FIN Scan will be logged if the packet has the FIN flag set.
• TCP Null Scan will be logged if the packet has no flags set.
–
When a new TCP connection initiation is attempted with something other than just the
SYN flag set.
–
When a packet with the SYN flag set is received within an established TCP session.
–
When a packet without the ACK flag set is received within an established TCP session.
• Invalid Sequence Packets Dropped – Incremented under the following conditions:
–
When a packet within an established connection is received where the sequence
number is less than the connection’s oldest unacknowledged sequence.
–
When a packet within an established connection is received where the sequence
number is greater than the connection’s oldest unacknowledged sequence + the
connection’s last advertised window size.
• Invalid Acknowledgement Packets Dropped - Incremented under the following
conditions:
–
When a packet is received with the ACK flag set, and with neither the RST or SYN flags
set, but the SYN Cookie is determined to be invalid (while SYN Flood protection is
enabled).
–
When a packet’s ACK value (adjusted by the sequence number randomization offset)
is less than the connection’s oldest unacknowledged sequence number.
–
When a packet’s ACK value (adjusted by the sequence number randomization offset)
is greater than the connection’s next expected sequence number.
TCP Settings


















