User Management
605
SonicOS Enhanced 4.0 Administrator Guide
• Samba SMB: Development information is available at http://us5.samba.org/samba/
• Novell eDirectory: LDAP integration information is available at http://www.novell.com/
documentation/edir873/index.html?page=/documentation/edir873/edir873/data/
h0000007.html
• User-defined schemas: See the documentation for your LDAP installation. You can also
see general information on LDAP at
http://rfc.net/rfc1777.html
Single Sign-On Overview
This section provides an introduction to the SonicWALL SonicOS Enhanced 4.0 Single Sign-
On feature. This section contains the following subsections:
• “What Is Single Sign-On?” section on page 605
• “Benefits” section on page 606
• “How Does Single Sign-On Work?” section on page 607
• “Platforms” section on page 606
What Is Single Sign-On?
Single Sign-On (SSO) is a transparent user authentication mechanism that provides privileged
access to multiple network resources with a single workstation login. SonicWALL PRO and TZ
series security appliances (SonicWALL security appliances) running SonicOS Enhanced 4.0
provide SSO functionality using the SonicWALL Single Sign-On Agent (SSO Agent) to identify
user activity based on workstation IP address. SSO is configured in the Users > Settings page
of the SonicOS management interface. SSO is separate from the Authentication method for
login settings, which can be used at the same time for authentication of VPN/L2TP client users
or administrative users.
SonicWALL SSO Agent identifies users by IP address using a SonicWALL ADConnector-
compatible protocol and automatically determines when a user has logged out to prevent
unauthorized access. Based on data from SonicWALL SSO Agent, the SonicWALL security
appliance queries LDAP or the local database to determine group membership. Memberships
are matched against policy, and based on user privileges, access is granted or denied. The
configured inactivity and session limit timers apply with SSO, though users who are logged out
are automatically and transparently logged back in when they send further traffic.
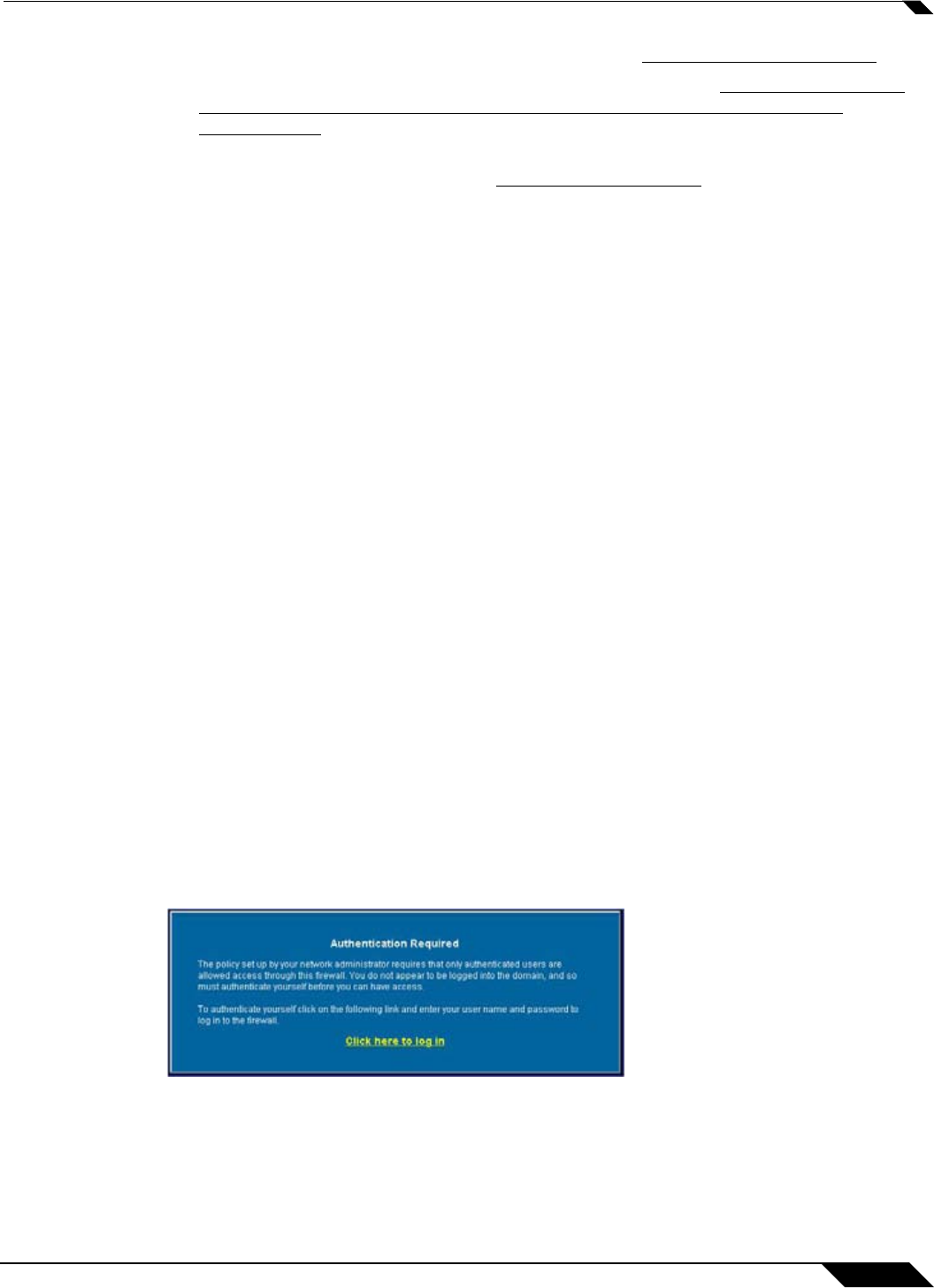
Users logged into a workstation directly but not logged into the domain will not be
authenticated. For users that are not logged into the domain, the following screen will display,
indicating that a manual login will be required for further authentication.


















