Network > NAT Policies
261
SonicOS Enhanced 4.0 Administrator Guide
3. Create two NAT entries to allow the two servers to initiate traffic to the public Internet.
4. Create two NAT entries to map the custom ports to the actual listening ports, and to map
the private IP addresses to the SonicWALL’s WAN IP address.
5. Create two access rule entries to allow any public user to connect to both servers via the
SonicWALL’s WAN IP address and the servers’ respective unique custom ports.
Step 1 Create a custom service for the different port. Go to the Firewall > Custom Services page and
click on the Add button. When the pop-up screen appears, give your custom services names
such as servone_public_port and servtwo_public_port, enter in 9100 and 9200 as the
starting and ending port, and choose TCP(6) as the protocol. When done, click on the OK
button to save the custom services.
Step 2 Go to the Network > Address Objects and click on the Add button at the bottom of the page.
In the Add Address Objects window, enter in a description for server’s private IP addresses,
choose Host from the drop-down box, enter the server’s private IP addresses, and select the
zone that the servers are in. When done, click on the OK button to create the range object.
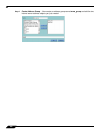
Step 3 Go to the Network > NAT Policies menu and click on the Add button. The Add NAT Policy
window is displayed. To create a NAT policy to allow the two servers to initiate traffic to the
public Internet using the SonicWALL security appliance’s WAN IP address, choose the
following from the drop-down boxes:
• Original Source: servone_private_ip
• Translated Source: WAN Primary IP
• Original Destination: Any
• Translated Destination: Original
• Original Service: Any
• Translated Service: Original
• Inbound Interface: Opt
• Outbound Interface: WAN
• Comment: Enter a short description
• Enable NAT Policy: Checked
• Create a reflective policy: Unchecked
And:
• Original Source: servtwo_private_ip
• Translated Source: WAN Primary IP
• Original Destination: Any
• Translated Destination: Original
• Original Service: Any
• Translated Service: Original
• Inbound Interface: Opt
• Outbound Interface: WAN
• Comment: Enter a short description
• Enable NAT Policy: Checked
• Create a reflective policy: Unchecked