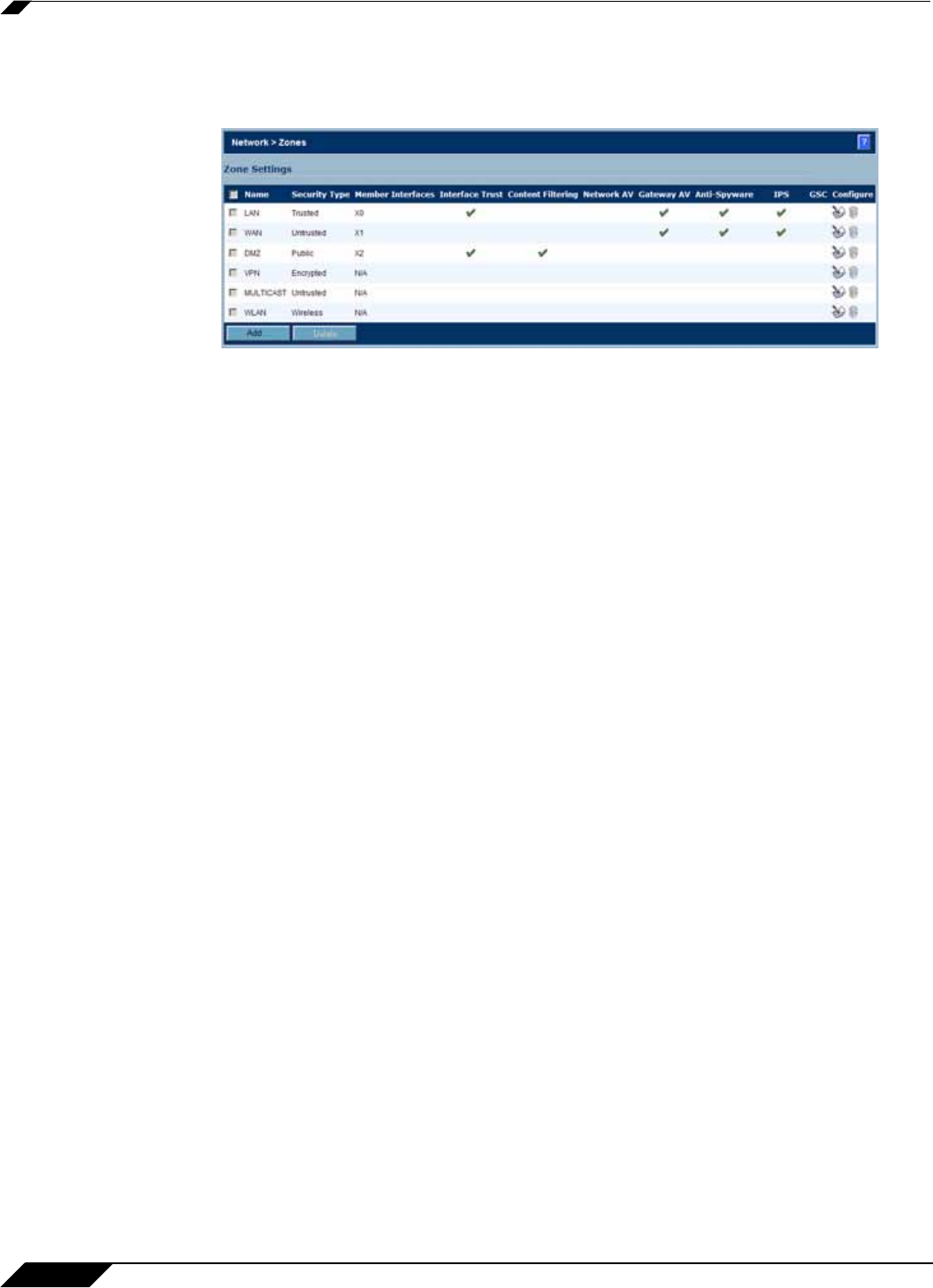
Network > Zones
192
SonicOS Enhanced 4.0 Administrator Guide
tunnels, which is a feature that users have long requested. SonicWALL security appliances can
also drive VPN traffic through the NAT policy and zone policy, since VPNs are now logically
grouped into their own VPN zone.
How Zones Work
An easy way to visualize how security zones work is to imagine a large new building, with
several rooms inside the building, and a group of new employees that do not know their way
around the building. This building has one or more exits, which can be thought of as the WAN
interfaces. The rooms within the building have one or more doors, which can be thought of as
interfaces. These rooms can be thought of as zones inside each room are a number of people.
The people are categorized and assigned to separate rooms within the building. People in each
room going to another room or leaving the building, must talk to a doorperson on the way out
of each room. This doorperson is the inter-zone/intra-zone security policy, and the
doorperson’s job to consult a list and make sure that the person is allowed to go to the other
room, or to leave the building. If the person is allowed (i.e. the security policy lets them), they
can leave the room via the door (the interface).
Upon entering the hallway, the person needs to consult with the hallway monitor to find out
where the room is, or where the door out of the building is located. This hallway monitor
provides the routing process because the monitor knows where all the rooms are located, and
how to get in and out of the building. The monitor also knows the addresses of any of the remote
offices, which can be considered the VPNs. If the building has more than one entrance/exit
(WAN interfaces), the hallway monitor can direct people to use the secondary entrance/exit,
depending upon how they’ve been told to do so (i.e. only in an emergency, or to distribute the
traffic in and out of the entrance/exits). This function can be thought of as WAN Load Balancing.
There are times that the rooms inside the building have more than one door, and times when
there are groups of people in the room who are not familiar with one another. In this example,
one group of people uses only one door, and another group uses the other door, even though
groups are all in the same room. Because they also don’t recognize each other, in order to
speak with someone in another group, the users must ask the doorperson (the security policy)
to point out which person in the other group is the one with whom they wish to speak. The
doorperson has the option to not let one group of people talk to the other groups in the room.
This is an example of when zones have more than one interface bound to them, and when intra-
zone traffic is not allowed.
Sometimes, people will wish to visit remote offices, and people may arrive from remote offices
to visit people in specific rooms in the building. These are the VPN tunnels. The hallway and
doorway monitors check to see if this is allowed or not, and allow traffic through. The
doorperson can also elect to force people to put on a costume before traveling to another room,
or to exit, or to another remote office. This hides the true identity of the person, masquerading
the person as someone else. This process can be thought of as the NAT policy.


















