Network > NAT Policies
251
SonicOS Enhanced 4.0 Administrator Guide
This document details how to configure the necessary NAT, load balancing, health check,
logging, and firewall rules to allow systems from the public Internet to access a Virtual IP (VIP)
that maps to one or more internal systems, such as Web servers, FTP servers, or SonicWALL
SSL-VPN appliances. This Virtual IP may be independent of the SonicWALL appliance or it may
be shared, assuming the SonicWALL appliance itself is not using the port(s) in question.
The examples in this document use two SonicWALL PRO 4100 appliances in high-availability
mode, two generic Web servers, and two SonicWALL SSL-VPN 2000 appliances. Please note
that it is not necessary to have two appliances to perform NAT/LB – it is just another layer of
protection that can be easily added to your environment to assure uptime to critical internal
resources that have high uptime requirements (typically a driving factor in load balancing
systems in the first place).
Please note that the load balancing capability in SonicOS Enhanced 4.0, while fairly basic, will
satisfy the requirements for many customer network deployments. Customers with
environments needing more granular load balancing, persistence, and health-check
mechanisms are advised to use a dedicated third-party load balancing appliance (prices run
from US$4,000 to US$25,000 per device).
NAT LB Mechanisms
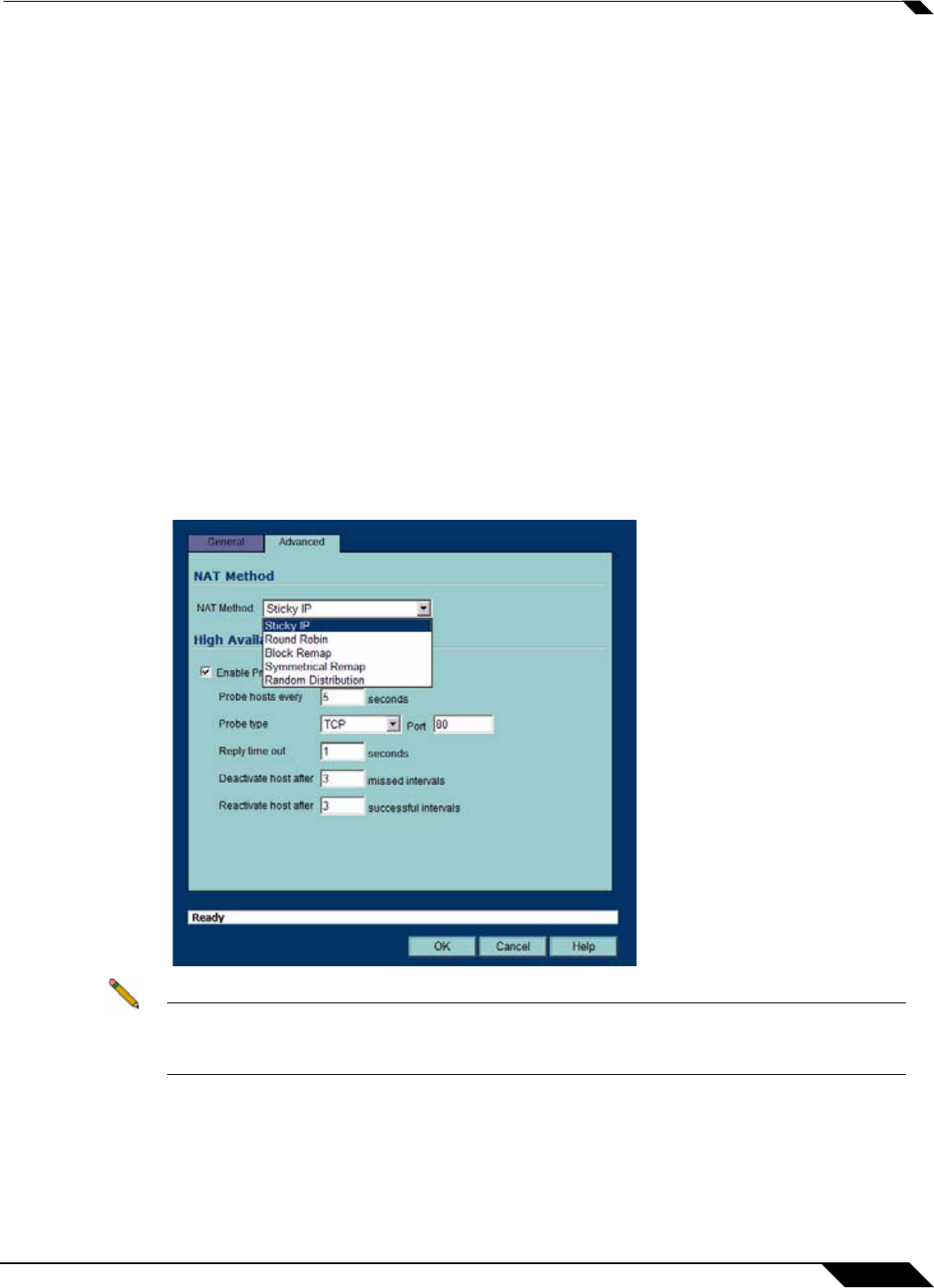
NAT load balancing is configured on the Advanced tab of a NAT policy.
Note This tab can only be activated when a group is specified in one of the drop-down fields on
the General tab of a NAT Policy. Otherwise, the NAT policy defaults to Sticky IP as the NAT
method.
SonicOS offers the following NAT methods:
• Sticky IP – Source IP always connects to the same Destination IP (assuming it is alive).
This method is best for publicly hosted sites requiring connection persistence, such as Web
applications, Web forms, or shopping cart applications. This is the default mechanism, and
is recommended for most deployments.


















