Network > Address Objects
217
SonicOS Enhanced 4.0 Administrator Guide
Blocking All Protocol Access to a Domain using FQDN DAOs
There might be instances where you wish to block all protocol access to a particular destination
IP because of non-standard ports of operations, unknown protocol use, or intentional traffic
obscuration through encryption, tunneling, or both. An example would be a user who has set
up an HTTPS proxy server (or other method of port-forwarding/tunneling on “trusted” ports like
53, 80, 443, as well as nonstandard ports, like 5734, 23221, and 63466) on his DSL or cable
modem home network for the purpose of obscuring his traffic by tunneling it through his home
network. The lack of port predictability is usually further complicated by the dynamic addressing
of these networks, making the IP address equally unpredictable.
Since these scenarios generally employ dynamic DNS (DDNS) registrations for the purpose of
allowing users to locate the home network, FQDN AOs can be put to aggressive use to block
access to all hosts within a DDNS registrar.
Note A DDNS target is used in this example for illustration. Non-DDNS target domains can be
used just as well.
Assumptions
• The SonicWALL firewall is configured to use DNS server 10.50.165.3, 10.50.128.53
• The SonicWALL is providing DHCP leases to all firewalled users. All hosts on the network
use the configured DNS servers above for resolution.
–
DNS communications to unsanctioned DNS servers can optionally be blocked with
Access Rules, as described in the ‘Enforcing the use of sanctioned servers on the
network’ section.
• The DSL home user is registering the hostname moosifer.dyndns.org with the DDNS
provider DynDNS. For this session, the ISP assigned the DSL connection the address
71.35.249.153.
–
A wildcard FQDN AO is used for illustration because other hostnames could easily be
registered for the same IP address. Entries for other DDNS providers could also be
added, as needed.
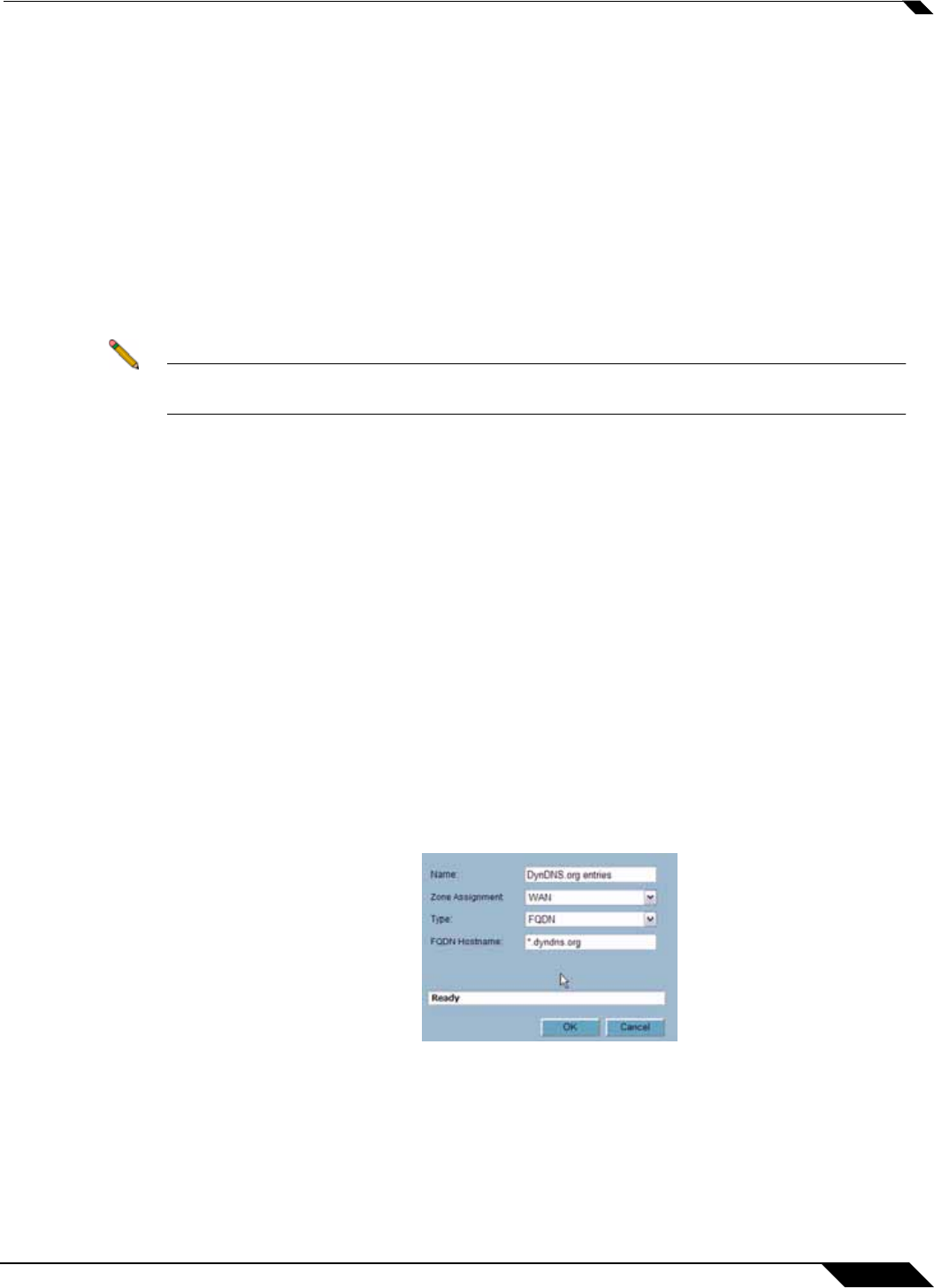
Step 1 – Create the FQDN Address Object
• From Network > Address Objects, select Add and create the following Address Object:
• When first created, this entry will resolve only to the address for dyndns.org, e.g.
63.208.196.110.


















