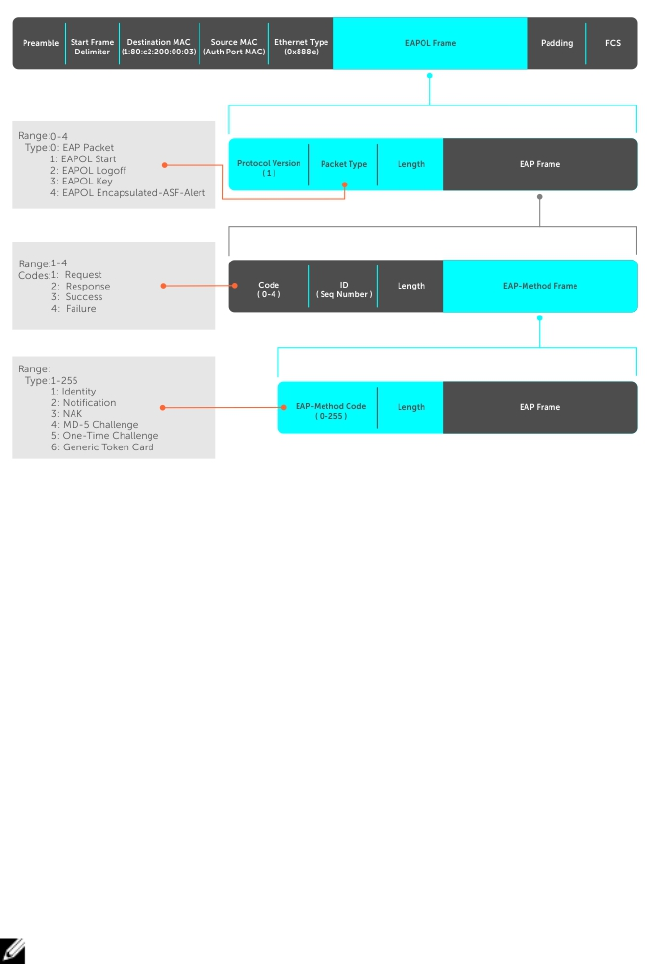
Figure 3. EAP Frames Encapsulated in Ethernet and RADUIS
The authentication process involves three devices:
• The device attempting to access the network is the supplicant. The supplicant is not allowed to
communicate on the network until the authenticator authorizes the port. It can only communicate
with the authenticator in response to 802.1X requests.
• The device with which the supplicant communicates is the authenticator. The authenticator is the
gate keeper of the network. It translates and forwards requests and responses between the
authentication server and the supplicant. The authenticator also changes the status of the port based
on the results of the authentication process. The Dell Networking switch is the authenticator.
• The authentication-server selects the authentication method, verifies the information the supplicant
provides, and grants it network access privileges.
Ports can be in one of two states:
• Ports are in an unauthorized state by default. In this state, non-802.1X traffic cannot be forwarded in
or out of the port.
• The authenticator changes the port state to authorized if the server can authenticate the supplicant.
In this state, network traffic can be forwarded normally.
NOTE: The Z9500 places 802.1X-enabled ports in the unauthorized state by default.
The Port-Authentication Process
The authentication process begins when the authenticator senses that a link status has changed from
down to up:
1. When the authenticator senses a link state change, it requests that the supplicant identify itself using
an EAP Identity Request frame.
2. The supplicant responds with its identity in an EAP Response Identity frame.
802.1X
79


















