SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
299
Log > View
SonicOS Log Entries
Each log entry contains the date and time of the event and a brief message describing the event. It is
also possible to copy the log entries from the management interface and paste into a report. The
SonicWALL security appliance manages log events in the following manner:
• Dropped TCP, UDP, or ICMP packets
When IP packets are blocked by the SonicWALL security appliance, dropped TCP, UDP and
ICMP messages are displayed. The messages include the source and destination IP addresses of
the packet. The TCP or UDP port number or the ICMP code follows the IP address. Log messages
usually include the name of the service in quotation marks.
• Blocked Web Sites
When a computer attempts to connect to the blocked site or newsgroup, a log event is displayed.
The computer’s IP address, Ethernet address, the name of the blocked Web site, and the Content
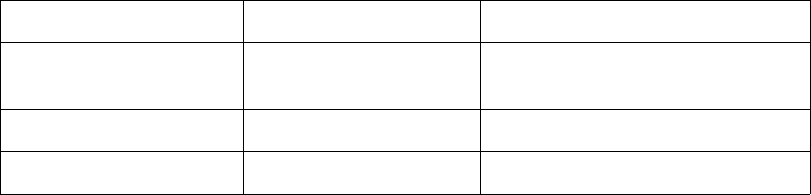
Filter List Code is displayed. Code definitions for the 12 Content Filter List categories are
displayed in the table below:
• Blocked Java, etc.
When ActiveX, Java or Web cookies are blocked, messages with the source and destination IP
addresses of the connection attempt is displayed.
• Ping of Death, IP Spoof, and SYN Flood Attacks
The IP address of the machine under attack and the source of the attack is displayed. In most
attacks, the source address shown is fake and does not reflect the real source of the attack.
9
Tip: Some network conditions can produce network traffic that appears to be an attack, even if no one
is deliberately attacking the LAN. Verify the log messages with SonicWALL Tech Support before
contacting your ISP to determine the source of the attack.
Refresh
To update log messages, clicking the Refresh button.
Clear Log
Clicking Clear Log deletes the contents of the log.
E-mail Log
If you have configured the SonicWALL security appliance to e-mail log files, clicking E-mail Log
sends the current log files to the e-mail address specified in the Log > Automation > E-mail section.
1. Violence/Hate/Racism 5. Weapons 9. Illegal Skills/Questionable Skills
2. Intimate Apparel/
Swimsuit
6. Adult/Mature Content 10. Sex Education
3. Nudism 7. Cult/Occult 11. Gambling
4. Pornography 8. Drugs/Illegal Drugs 12. Alcohol/Tobacco


















