230
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE
C
HAPTER
37:
Configuring Advanced VPN Settings
keep alive that acts as a “heartbeat” sent by the VPN device behind the NAT or NAPT device. The
“keepalive” is silently discarded by the IPSec peer.
Selecting Enable NAT Traversal allows VPN tunnels to support this protocol, and log messages
are generated by the SonicWALL when a IPSec Security Gateway is detected behind a NAT/
NAPT device. The following log messages are found on the View > Log page:
Peer IPSec Gateway behind a NAT/NAPT device
Local IPSec Security Gateway behind a NAT/NAPT device
No NAT/NAPT device detected between IPSec Security
Peer IPSec Security Gateway doesn’t support VPN NAT Traversal
• Keep Alive interval (seconds) - the default value is 240 seconds (4 minutes). If Enable Keep
Alive is selected on the Advanced VPN Settings page, a new negotiation begins if the previous
VPN Policy was deleted by Dead Peer Detection (DPD).
• Enable IKE Dead Peer Detection - select if you want inactive VPN tunnels to be dropped by the
SonicWALL. Enter the number of seconds between “heartbeats” in the Dead Peer Detection
Interval (seconds) field. The default value is 60 seconds. Enter the number of missed heartbeats
in the Failure Trigger Level (missed heartbeats) field. The default value is 3. If the trigger level is
reached, the VPN connection is dropped by the SonicWALL security appliance. The SonicWALL
uses a UDP packet protected by Phase 1 Encryption as the heartbeat.
• VPN Single Armed mode (stand-alone VPN gateway) -
• Clean up Active tunnels when Peer Gateway DNS name resolves to a different IP address -
Breaks down SAs associated with old IP addresses and reconnects to the peer gateway.
• Preserve IKE Port for Pass Through Connections - Preserves UDP 500/4500 source port and
IP address information for pass-through VPN connections.
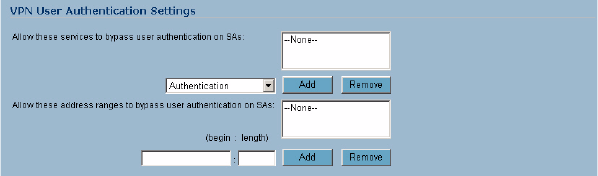
VPN User Authentication Settings
• Allow these services to bypass user authentication on SAs - this feature allows VPN users
without authentication to access the specified services. To add a service, select the service from
the menu and click Add. The service is added to the Allow these services to bypass user
authentication on SAs list. To remove a service, select the service in the Allow these services
to bypass user authentication on VPN SAs list and click Remove.
• Allow these address ranges to bypass user authentication on SAs - this feature allows the
specified IP address or IP address range to bypass user authentication on VPN connections. To
add an IP address, enter the single IP address in the text box, then click Add. To add an IP
address range, enter the range starting IP address in the first field and the length in the text field
(up to the last three numbers of the IP address).


















