46 IBM Tivoli Remote Control Across Firewalls
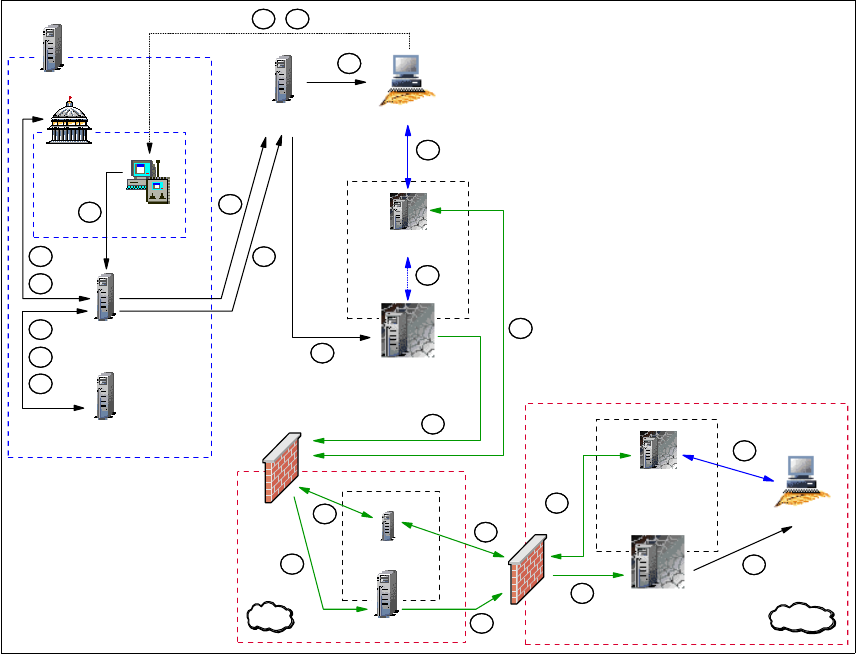
Figure 1-8 RC session data flow in an RC Proxy-TFST/single-TMR environment
Based on Figure 1-8, here we detail each step from the time the Tivoli
Administrator opens a Remote Control Tool until the connection is established
between the Controller and the Target through the Remote Control Proxies.
The legend used in Figure 1-8 is explained as follows:
Steps A, B,C, D, E, F, G and I remain the same as for a Remote Control session
in single-TMR environment without firewall restriction. Refer to “Data flow for
single-TMR session” on page 14 for detailed information about these steps.
The remaining steps are different and are defined as follows:
H This step remains almost the same as for a standard session in a
non-secure environment. However, in a standard process the
nd_start_target method is sent to the Target using the standard
RC Server
Controller
Target
RC Tool
PR
TMR Server
Endpoint Mgr
Endpoint GW
H
B
A
D
E
C
G
F
I
J
I
H
A
H
J
J
Firewall
DMZ
RC Contr. Proxy
Gateway Proxy
H
J
J
RC Target Proxy
Endpoint Proxy
Firewall
External
Relay 1 TFST
Relay 2 TFST
J
J
H
H
H


















