36 IBM Tivoli Remote Control Across Firewalls
The RC Target Proxy emulates the Target located in another network zone to the
Controller. The Target Proxy must be able to communicate with the Controller
without any firewall constraints, and thus must be located in the same network
zone as the Controller.
On the other side, the RC Controller Proxy emulates the Controller located in
another zone to the Target. The Controller Proxy must be able to communicate
with the Target without any firewall constraints, and thus must be located in the
same network zone as the Target.
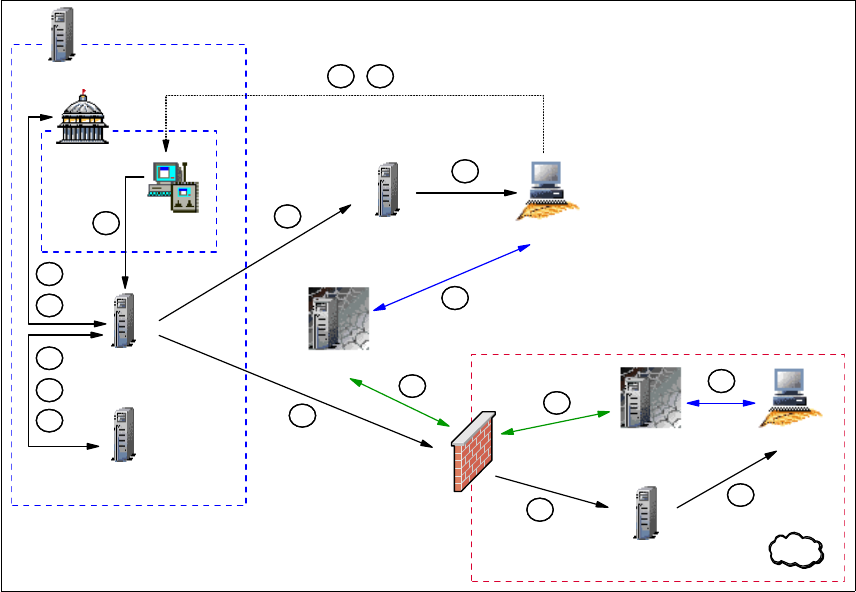
Data flow for RC Proxy Standalone/single-TMR session
Figure 1-6 shows in detail how a Remote Control session works using a Remote
Control Proxy Standalone architecture in a single-TMR environment with firewall
restrictions.
Figure 1-6 RC session data flow in an RC Proxy Standalone/single-TMR
RC Server
Controller
Target
RC Tool
PR
TMR Server
Endpoint Mgr
Endpoint GW
Endpoint GW
H
B
A
D
E
C
G
F
I
J
I
H
A
H
J
J
Firewall
DMZ
J
RC Target Proxy
RC Controller Proxy


















