Chapter 1. Remote Control sessions overview 11
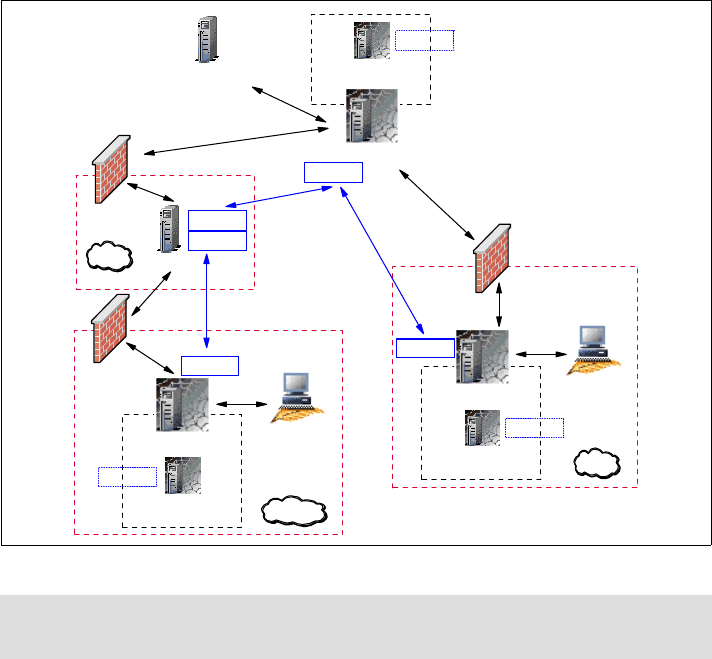
Figure 1-1 Parent-Child hierarchy in RC Proxy-TFST architecture
1.1.5 Proxy connection types
In some secure environments, the firewall’s constraints are so high that only
communications from the more secure environment to the less secure
environments are allowed. Either the Tivoli Firewall Security Toolbox or the
Remote Control Proxies communications are designed to support those
constraints. Even though we explain the proxy connection types in this section
using the Tivoli Firewall Security Toolbox components, the same is valid for the
Remote Control Proxies.
Different types of communications are available. The key point is which
component initiates the communication:
Note: Understanding this hierarchy is important when you install and
configure the components.
TMR Server
Endpoint GW
RC Target Proxy
Endpoint Proxy
DMZ
Firewall
Relay
Endpoint
Firewall
RC Contr. Proxy
Gateway Proxy
External
Endpoint
Firewall
DMZ
RC Contr. Proxy
Gateway Proxy
Parent
Child
Child
Child
Parent
Parent
Child
Child


















