120 IBM Tivoli Remote Control Across Firewalls
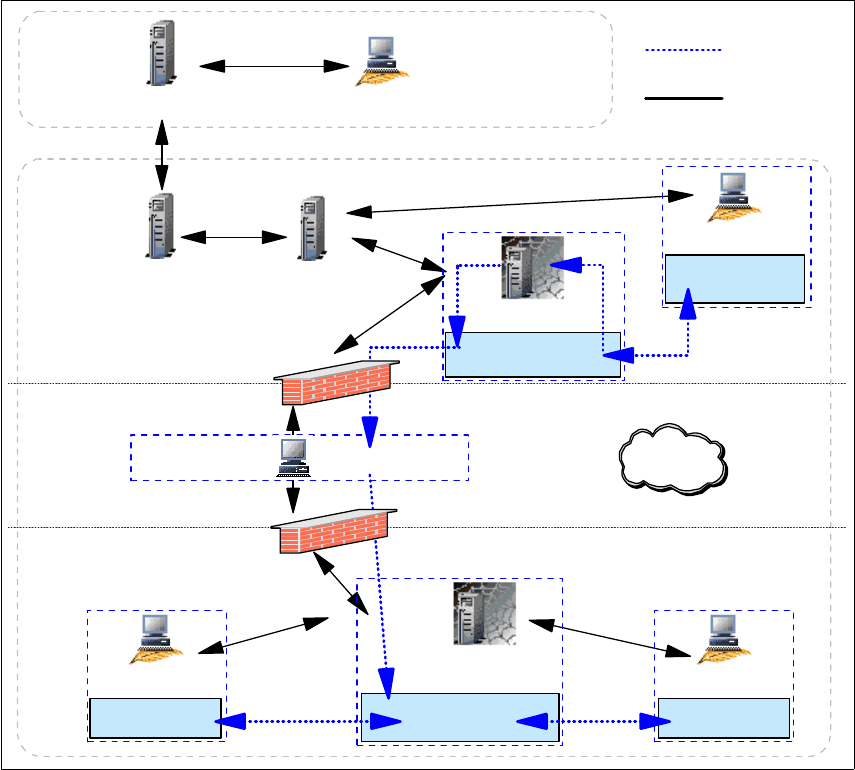
Figure 4-2 Remote Control Proxy Implementation in a TFST environment
Based on Figure 4-2, we configured our testing scenario as follows:
An RC Target Proxy needs to be installed on the same machine as the
Endpoint Proxy. Because this Endpoint Proxy is a Parent in the TFST
structure, this RC Target Proxy automatically becomes a Parent.
Per security guidelines, the communication is defined as unidirectional.
Therefore, only the RC Target Proxy on the secure zone can be the
connection initiator.
Endpoint
Windows TS server
Endpoint Gateway
AIX 5.1 - tic01010
Hub TMR server
AIX 5.1 - tic01002
Firewall 1
De-Militarized
Zone (DMZ)
Spoke TMR server
AIX 5.1 - tic01010
TMR Spoke
TMR Hub
Endpoint Proxy
Windows - tic01003
Gateway Proxy
Windows - tic01005
Endpoint
Windows - tic01006
Firewall 2
Controller Proxy
- child -
Remote Control
Controller
Target Proxy
parent - unidirectional
Target Endpoint
Endpoint
Windows - tic01007
Target Endpoint
Endpoint
Windows - tic01007
Remote Control
Connections
Framework
Connections
Relay inst2 - tic01004
Relay inst1 - tic01004


















