40 IBM Tivoli Remote Control Across Firewalls
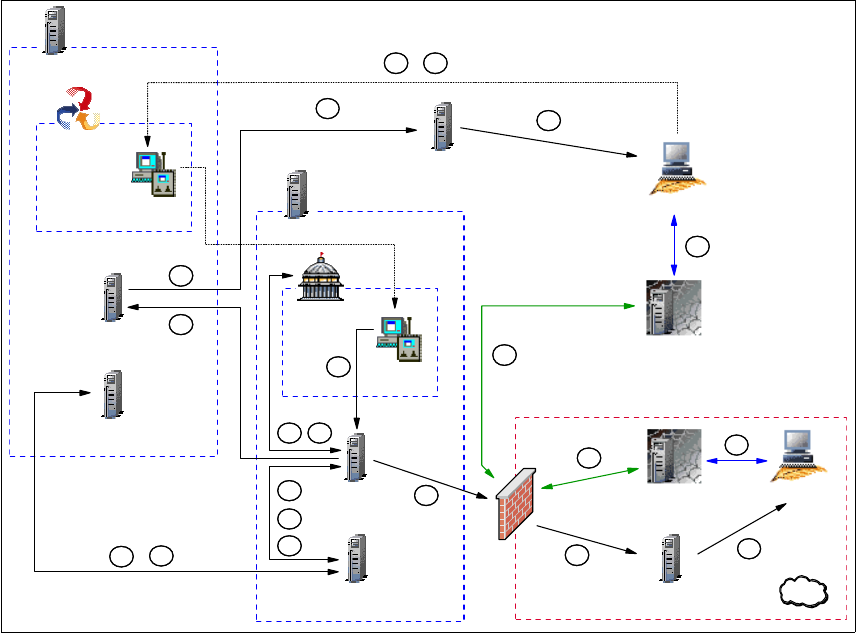
Figure 1-7 RC session data flow in an RC Proxy Standalone/multi-TMR
Based on Figure 1-7, here we detail each step from the time the Tivoli
Administrator opens a Remote Control Tool until the connection is established
between the Controller and the Target using the Remote Control Proxies.
The legend used in Figure 1-7 is explained as follows:
Steps A, B,C, D, E, F, G, H, I, J and K are similar to a Remote Control session in
multi-TMR environment without firewall restriction. Refer to “Data flow for a
multi-TMR session” on page 21 for detailed information about these steps.
The remaining step is different and defined as follows:
L Both sessions on the Target and on the Controller are now started.
At this step, the Controller need to establish the link to control the
Target. The rc_def_proxy policy has been configured to force the
usage of the Remote Control Proxies and the Remote Control Server
Spoke RC
Server
Spoke RC
Tool
Spoke
PR
Spoke TMR Server
Spoke Endpoint Mgr
HUB
Endpoint GW
B
K
Spoke RC
Tool
HUB TMR Server
G
HUB RCL
Collection
HUB RC
Server
C
D
A
E
F
H
I
K
K
HUB Endpoint Mgr
A
Controller
K
Target
Endpoint GW
J
J
Firewall
DMZ
RC Controller Proxy
L
L
J
RC Target Proxy
L
L


















