9-6
Cisco ONS 15454 Reference Manual, R8.5.x
78-18106-01
Chapter 9 Security
9.2.2 Security Policies
9.2.2 Security Policies
Users with Superuser security privileges can provision security policies on the ONS 15454. These
security policies include idle user timeouts, password changes, password aging, and user lockout
parameters. In addition, a Superuser can access the ONS 15454 through the TCC2/TCC2P RJ-45 port,
the backplane LAN connection, or both. If enabled in the NE defaults, superusers can be configured to
override the inactive user timeout interval.
9.2.2.1 Superuser Privileges for Provisioning Users
Superusers can grant permission to Provisioning users to retrieve audit logs, restore databases, clear
performance monitoring (PM) parameters, activate software loads, and revert software loads. These
privileges can only be set using CTC network element (NE) defaults, except the PM clearing privilege,
which can be granted to a Provisioning user using the CTC Provisioning> Security > Access tabs. For
more information about setting up Superuser privileges, refer to the Cisco ONS 15454 Procedure Guide.
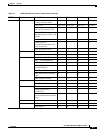
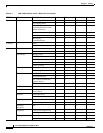
Provisioning Security Users: Create/Delete — — — X
Users: Edit Same user Same user Same user All users
Active logins:
Logout/Retrieve Last Activity
Time
———X
Policy: Change — — — X
Alarm Profiles Store/Delete
3
—— X X
New/Load/Compare/
Available/Usage
XXXX
BLSR Create/Delete/Edit/Upgrade — — X X
Overhead Circuits Create/Delete/Edit/Merge — — X X
Search X X X X
Provisionable
Patchcords (PPC)
Create/Edit/Delete — — X X
Server Trails Create/Edit/Delete — — X X
VLAN DB Profile Load/Store/Merge/Circuits X X X X
Maintenance Software Download/Cancel — X X X
Diagnostic OSPF Node Information:
Retrieve/Clear
XXXX
APC Run APC/Disable APC — — — X
Refresh XXXX
1. X indicates that the user can perform the actions.
2. — indicates that the privilege to perform an action is not available to the user.
3. The action buttons in the subtab are active for all users, but the actions can be completely performed only by the users with the required security levels.
Table 9-2 ONS 15454 Security Levels—Network View (continued)
CTC Tab Subtab [Subtab]: Actions Retrieve Maintenance Provisioning Superuser