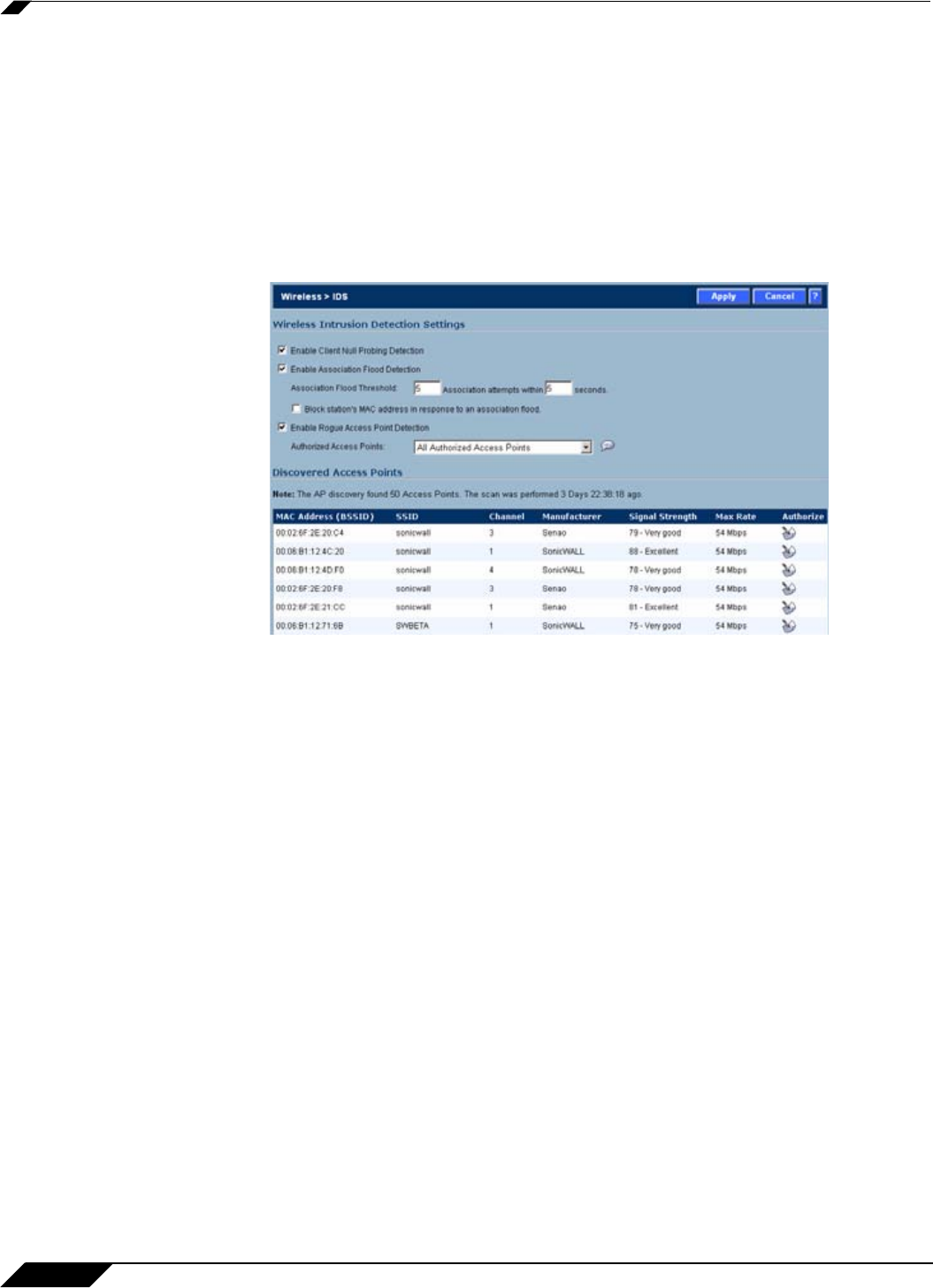
Wireless > IDS
348
SonicOS Enhanced 4.0 Administrator Guide
Access Point IDS
When the Radio Role of the wireless security appliance is set to Access Point mode, all three
types of WIDS services are available, but Rogue Access Point detection, by default, acts in a
passive mode (passively listening to other Access Point Beacon frames only on the selected
channel of operation). Selecting Scan Now momentarily changes the Radio Role to allow the
wireless security appliance to perform an active scan, and may cause a brief loss of
connectivity for associated wireless clients. While in Access Point mode, the Scan Now
function should only be used if no clients are actively associated, or if the possibility of client
interruption is acceptable.
Enable Client Null Probing
Enabling this setting allows the wireless security appliance to detect and log Null Probes, such
as those used by Netstumbler and other similar tools.
Association Flood Detection
Association Flood is a type of Wireless Denial of Service attack intended to interrupt wireless
services by depleting the resources of a wireless Access Point. An attacker can employ a
variety of tools to establish associations, and consequently association IDs, with an access
point until it reaches its association limit (generally set to 255). Once association saturation
occurs, the access point discards further association attempts until existing associations are
terminated.
Association Flood Detection allows thresholds to be set limiting the number of association
attempts a client makes in a given span of time before its activities are considered hostile.
Association attempts default to a value of 5 (minimum value is 1, maximum value is 100) within
and the time period defaults to a value of 5 seconds (minimum value is 1 second, maximum
value is 999 seconds). If association attempts exceed the set thresholds, an event is logged
according to log settings.
If the Block station's MAC address in response to an association flood option is selected
and MAC Filtering is enabled, then in addition to logging actions, the wireless security
appliance takes the countermeasure of dynamically adding the MAC address to the MAC filter
list. Any future Denial of Service attempts by the attacker are then blocked.


















