6-13
Cisco ASA 5500 Series Adaptive Security Appliance Getting Started Guide
78-17611-01
Chapter 6 Scenario: DMZ Configuration
Configuring the Security Appliance for a DMZ Deployment
In this procedure, you configure a Network Address Translation (NAT) rule that
associates IP addresses from this pool with the inside clients so they can
communicate securely with the DMZ web server.
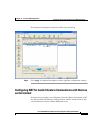
To configure NAT between the inside interface and the DMZ interface, perform
the following steps starting from the main ASDM window:
Step 1 In the main ASDM window, click the Configuration tool.
Step 2 In the Features pane, click NAT.
Step 3 From the Add drop-down list, choose Add Dynamic NAT Rule.
The Add Dynamic NAT Rule dialog box appears.
Step 4 In the Real Address area, specify the IP address to be translated. For this scenario,
address translation for inside clients is done according to the IP address of the
subnet.
a. From the Interface drop-down list, choose the Inside interface.
b. Enter the IP address of the client or network. In this scenario, the IP address
of the network is 10.10.10.0.
c. From the Netmask drop-down list, choose the Netmask. In this scenario, the
netmask is 255.255.255.0.
Step 5 In the Dynamic Translation area:
a. From the Interface drop-down list, choose the DMZ interface.
b. To specify the address pool to be used for this Dynamic NAT rule, check the
Select check box next to Global Pool ID. In this scenario, the IP pool ID is
200.
In this scenario, the IP pool that we want to use is already created. If it was
not already created, you would click Add to create a new IP pool.