36 | Configuring NAT Mode Gateway
Configuring NAT Mode Gateway
This section provides an overview of a Dell SonicWALL NSA
appliance operating as a single network gateway in NAT mode,
which is the default mode for a newly configured
NSA appliance. This section is relevant to administrators
following deployment Scenario A.
Note: No additional configuration is necessary to deploy your
appliance as a single network gateway in Many-to-One
NAT mode.
Overview of NAT Mode
Network Address Translation (NAT) allows private IP addresses
on internal networks to be mapped to at least one public IP
address on the WAN interface of the Dell SonicWALL security
appliance. Outbound traffic from the internal network uses
many-to-one NAT address mappings for their LANs, WLANs,
and other internal networks.
All traffic in SonicOS must go through both an access rule and a
NAT policy, a fundamental part of the NAT Mode architecture.
The NAT policy is even used for traffic that needs no IP address
translation, such as traffic traveling between two different LAN
interfaces, traffic on the simplest types of VPNs, or through
Layer 2 Bridge Mode / Transparent Mode configurations.
The Dell SonicWALL NSA appliance ships with the internal
DHCP server active on the LAN port. However, if a DHCP
server is already active on your LAN, the Dell SonicWALL
appliance will disable its own DHCP server to prevent conflicts.
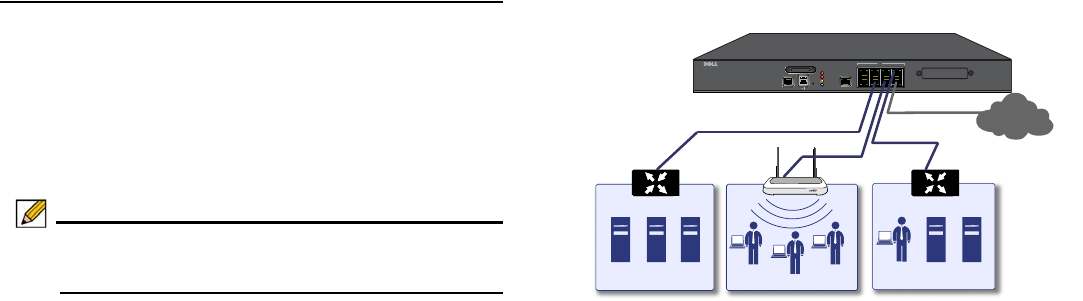
As shown in the illustration on this page, ports X1 and X0 are
preconfigured as WAN and LAN, respectively. The remaining
ports (X2-X7) can be configured to meet the needs of your
network. In the example diagram, certain interfaces are
configured for specific zones:
•X1—WAN
• X0—LAN
• X3—Wireless LAN
•X5—DMZ
LAN Zone
DMZ Zone
WLAN Zone
SonicPoint
Internet
ISP 1
Dell SonicWALL NSA Appliance
X1
X0
X3
X5
SonicWALL NSA 2600
CONSOLE
SDHC
MGMT
X6 X4
1GE
X2 X0
M0
X1X3X5X7
ALARM
M0
TEST
PWR
Expansion Module


















