Procedures for Out-of-Band and Inline NAC
Enterasys NAC Design Guide 5-15
A device or class of devices
needs to be restricted network
access (“blacklisted”) in a
particular Security Domain or in
all Security Domains.
Denying access or quarantining the
MAC addresses of laptops used by
guests or contractors in those areas of
the network designated to provide
access only to trusted employees.
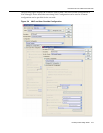
In NAC Manager, create a MAC override with the
following attributes:
• Specify either full MAC address or MAC
address OUI.
• Select the Security Domain or all Security
Domains for the MAC override scope.
For the assessment, authentication, and
authorization configuration, choose a NAC
Configuration or specify a custom configuration
with the following parameters:
• Select either the “Proxy RADIUS request to a
RADIUS Server” radio button or the “Reject”
radio button.
• Check “Authorize MAC Authentication
Requests Locally” so MAC authentication
attempts by these devices are assigned the
Accept Policy.
• Check “Replace RADIUS Policy with Accept
Policy” so the policy information returned from
the RADIUS server will be overwritten by the
Accept Policy.
• Select “Quarantine” as the Accept Policy.
• Deselect the “Enable Assessment” checkbox
so the end-systems are not assessed for
security posture compliance
Note that NetSight ASM leverages global ASM
MAC overrides with this configuration to
establish location-independent quarantine
actions by quarantining end-systems that have
violated the network security policy.
To deny untrusted end-systems network access
by sending the switch a RADIUS Access-Reject
message (instead of quarantining), make the
following change to the authorization
configuration for the MAC override:
• Select the “Reject“ radio button instead of
selecting the “Proxy RADIUS request to a
RADIUS Server“ radio button.
Table 5-3 MAC Override Configuration Guidelines (continued)
Network Scenario Examples Security Domain Configuration