Scenario 4: VPN Remote Access
Enterasys NAC Design Guide 3-11
Scenario 3 Implementation
Inthenon‐intelligentaccessedgeusescenario,thefiveNACfunctionsareimplementedinthe
followingmanner:
1.Detection‐Theuserʹsend‐systemconnectstothenetworkandtransmitsdatatrafficontothe
networkthattraversestheNACController.ThistrafficissourcedfromaMACaddressorIP
addressnotpreviouslyseenbythecontroller.
2.Authentication‐OneoftwoconfigurationsmaybeimplementedontheNACControllerfor
enduserauthentication.Authenticationcanbedisabledaltogether,trustingthatthedownstream
infrastructuredevicesauthenticated theend‐systemtothenetwork(802.1Xauthenticationtothe
wirelessLAN,web‐basedauthentication
tothewiredLAN).Alternatively,MACregistrationcan
beimplemented,whereanenduserusernameandpasswordand/orsponsorusernameand
passwordmustbevalidatedagainstabackendLDAP‐compliantdatabasebeforenetworkaccessis
permitted.
3.Assessment‐Aftertheidentityoftheend‐systemorenduserisvalidatedby
authentication,the
NACControllerrequestsanassessmentoftheend‐systemaccordingtopredefinedsecuritypolicy
parameters.Theassessmentcanbeagent‐basedoragent‐less,andisexecutedlocallybytheNAC
Controllerʹsassessmentfunctionalityand/orremotelybyapoolofassessmentservers.
4.Authorization‐Onceauthenticationandassessment
arecomplete,theNACController
allocatestheappropriatenetworkresourcestotheend‐systembasedonauthenticationand/or
assessmentresults.ThisisimplementedlocallyontheNACControllerbyassigningapolicyto
trafficsourcedfromthisend‐system.Ifauthenticationfailsand/ortheassessmentresultsindicate
anoncompliantend‐system,
theNACControllercaneitherdenytheend‐systemaccesstothe
networkorquarantinetheend‐systembyspecifyingaparticularpolicyontheNACController.
5.Remediation‐Whenthequarantinedenduseropensawebbrowsertoanywebsite,itstrafficis
dynamicallyredirectedtoaRemediationweb
pagethatdescribesthecomplianceviolationsand
providesremediationsstepsfortheusertoexecuteinordertoachievecompliance.Aftertaking
theappropriateremediationsteps,theenduserclicksonabuttononthewebpagetoreattempt
networkaccess,forcingthere‐assessmentoftheend‐system.At
thispoint,theEnterasysNAC
solutiontransitionstheend‐systemthroughtheentireNACcycleofdetection,authentication,
assessment,andauthorization,re‐assessingthesecuritypostureoftheend‐systemtodetermineif
theremediationtechniquesweresuccessfullyfollowed.Iftheend‐systemisnowcompliant,the
NACControllerauthorizesthe
end‐systemwiththeappropriateaccesspolicy.Iftheend‐systemis
notcompliant,theend‐systemisrestrictedaccesstothenetworkbyassigningapolicytotheend‐
systemontheNACController,andtheprocessstartsagain.
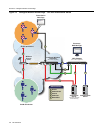
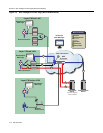
Scenario 4: VPN Remote Access
IntheVPNremoteaccessusescenario,VPNconcentratorsactasaterminationpointforremote
accessVPNtunnelsintotheenterprisenetwork.
Forthisusescenario,theNACControllerapplianceisdeployedtoauthorizeconnectingend‐
systemsonthenetworkandimplementnetworkaccesscontrol.
Thefollowingfigureillustrateshowthe
NACControllerandtheotherEnterasysNAC
componentsworktogetherinaVPNremoteaccessdeploymenttoprovideacomprehensiveNAC
solution.