Procedures for Out-of-Band and Inline NAC
5-8 Design Procedures
Area of the network that
provides access to a group of
users or devices that pose a
potentially high risk to the
security or stability of the
network.
• Switches that provide access to
guest users or contractors on a
corporate network. These users are
usually not directly under the
administrative control of IT
operations and pose additional risks
to the network.
• Switches that provide access to
users within an organization that are
allowed to engage in high risk
behaviors on the network, or are not
protected by security mechanisms
such as a firewall or Intrusion
Detection Systems (IDS). A sales
organization that uses the Internet
as a necessary part of their job, or a
branch office location that is not
protected by a firewall would both be
characterized as high risk groups of
users.
• Wireless Access Points (APs) that
are configured with an open wireless
network or a wireless network that is
secured through weak
authentication/encryption
mechanisms such as WEP. End-
systems on these networks pose a
greater risk to the organization
because access to the network by
untrusted users is easier.
Impose a more restrictive set of network
resources in the authorization of connecting end-
systems, and execute a thorough security
posture assessment of connecting end-systems
(if assessment is implemented on the network).
These measures limit the network exposure to
security threat propagation and protect against
network instability.
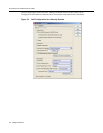
In NAC Manager, create a Security Domain with
the following configuration attributes:
• With the “Proxy RADIUS Request to a
RADIUS Server” radio button selected, check
the “Replace RADIUS Attributes with Accept
Policy” option and specify a restrictive policy
or VLAN in the Accept Policy field.
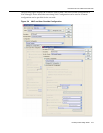
Furthermore, a more extensive Assessment
Configuration may be selected to scan these
devices with a larger set of assessment
parameters.
This allows the administrator to locally
authorize MAC authentication requests and
overwrite the policy information returned from
the RADIUS server with a more restrictive
policy.
• Configure the Accept Policy with a policy or
VLAN that provides more restrictive network
access for end-systems posing a higher risk.
Area of the network that is more
apt to affect the network's
overall security or stability.
• Switches that front-end a distribution
layer device that often crashes in the
event of security threats or other
events on the network. Assigning a
more restrictive policy to these end-
systems protects against the
instability of the infrastructure
devices.
Area of the network where
authentication is not deployed
and open network access is
available.
• Switches that provide access to
conference rooms, libraries, and
other areas commonly used by
untrusted users.
• Access points that provide guest
access to an open SSID.
Table 5-1 Security Domain Configuration Guidelines (continued)
Network Scenario Examples Security Domain Configuration