Procedures for Out-of-Band and Inline NAC
5-14 Design Procedures
ThefollowingtabledescribesscenarioswhereaMACoverridemaybeconfiguredforaparticular
end‐system.
Table 5-3 MAC Override Configuration Guidelines
Network Scenario Examples Security Domain Configuration
A device, or class of devices,
that utilize a distinct set of
parameters for authentication,
assessment, and authorization.
Allocating VoIP services to IP phones
on the network. For example, you could
create a MAC override where a
Polycom IP Phone, identified by the
MAC address OUI of the authenticating
end-system, is assigned to the IP
Phone policy or Voice VLAN and not
assessed for security posture
compliance when connecting to any
Security Domain.
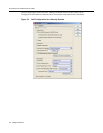
In NAC Manager, create a MAC override with the
following attributes:
• Specify either full MAC address or MAC
address OUI.
• Select the Security Domain or all Security
Domains for the MAC override scope.
For the assessment, authentication, and
authorization configuration, choose a NAC
Configuration or specify a custom configuration
with the following parameters:
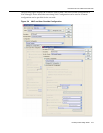
• Select either the “Proxy RADIUS request to a
RADIUS Server” radio button or the “Reject”
radio button.
• If the “Proxy RADIUS request to a RADIUS
Server” radio button is selected, check
“Authorize MAC Authentication Requests
Locally” if MAC authentication requests are to
be authorized, regardless of the MAC
authentication password.
• Check “Replace RADIUS Attributes with
Accept Policy” if the policy information
returned from the RADIUS server will be
overwritten by the Accept Policy.
• Format the Accept Policy with the policy or
VLAN.
• Check the “Enable Assessment” checkbox if
this device, or class of devices, is to be
assessed, and select the appropriate
Assessment Configuration for these devices.
• Specify the assessment and authorization
parameters such as assessment interval,
Quarantine Policy, and whether or not to
apply the Assessment Policy while the end-
system is being scanned.