Generating Random Numbers
18 RSA BSAFE Crypto-C Intel Hardware User’s Guide
Step 4: Update the Random Object
Step 4 is not needed for random number seeding in hardware.
Step 5: Generate Random Bytes
Generate the random bytes for the seed. In this example, you will have the Crypto-C
SDK generate
seedMaxLength
random bytes, storing the data in
seedBytes
. The last
parameter is a surrender context. In this case, generating random bytes should be
very quick, so you can pass in a properly cast
NULL_PTR.
Note:
If the Intel RNG is not present, or it returns an error, B_GenerateRandomBytes
will return a non-zero value. (For more information, see Appendix A, “Error
Codes”.) The appropriate action depends on the security needs of your
application.
Step 6: Destroy All Objects
Step 6a:Destroy the Algorithm Object
Destroy the algorithm object. This step will free any allocated memory used by
randomAlgorithm
. The memory is overwritten with zeros before it is deallocated, so
that any potentially sensitive information is not left in memory.
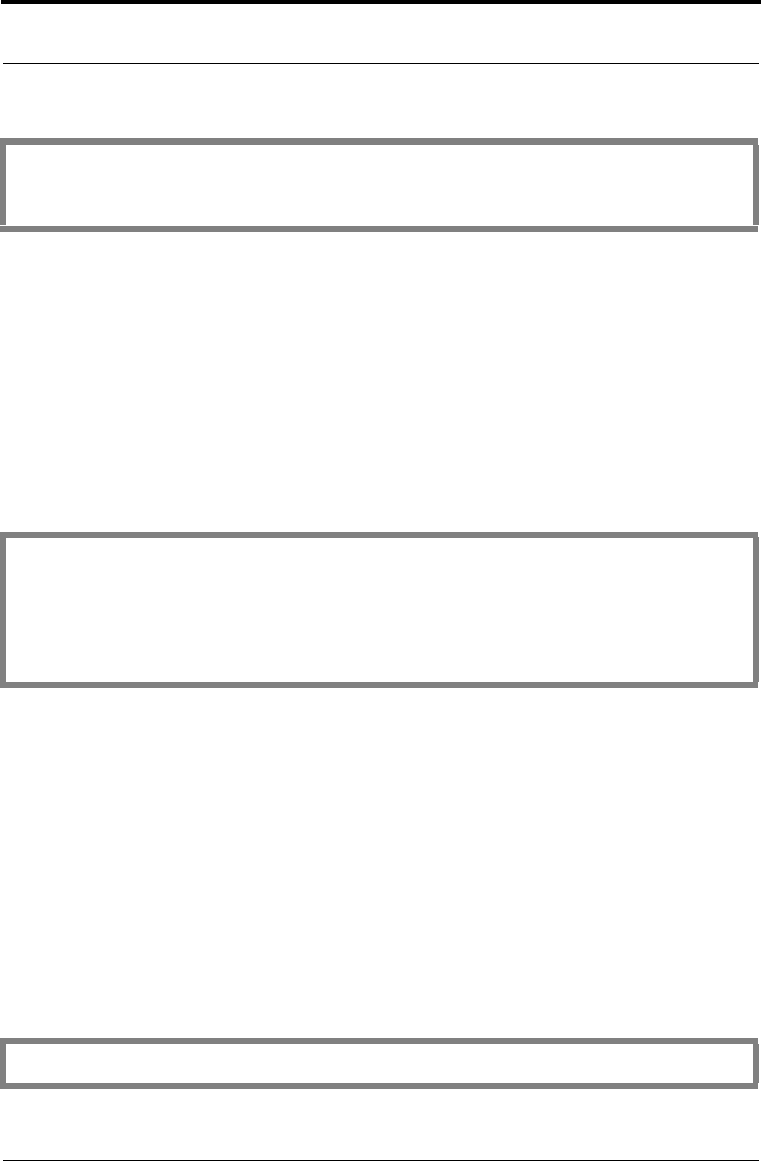
if ((status = B_RandomInit
(randomAlgorithm, CHOOSER, (A_SURRENDER_CTX *)NULL_PTR)) != 0)
break;
int seedBytes = 128;
if ((status = B_GenerateRandomBytes
(randomAlgorithm, seedBytes, seedMaxLength,
(A_SURRENDER_CTX *)NULL_PTR)) != 0)
break;
B_DestroyAlgorithmObject (&randomAlgorithm);


















