15-11
Cisco Security Appliance Command Line Configuration Guide
OL-12172-01
Chapter 15 Firewall Mode Overview
Transparent Mode Overview
How Data Moves Through the Transparent Firewall
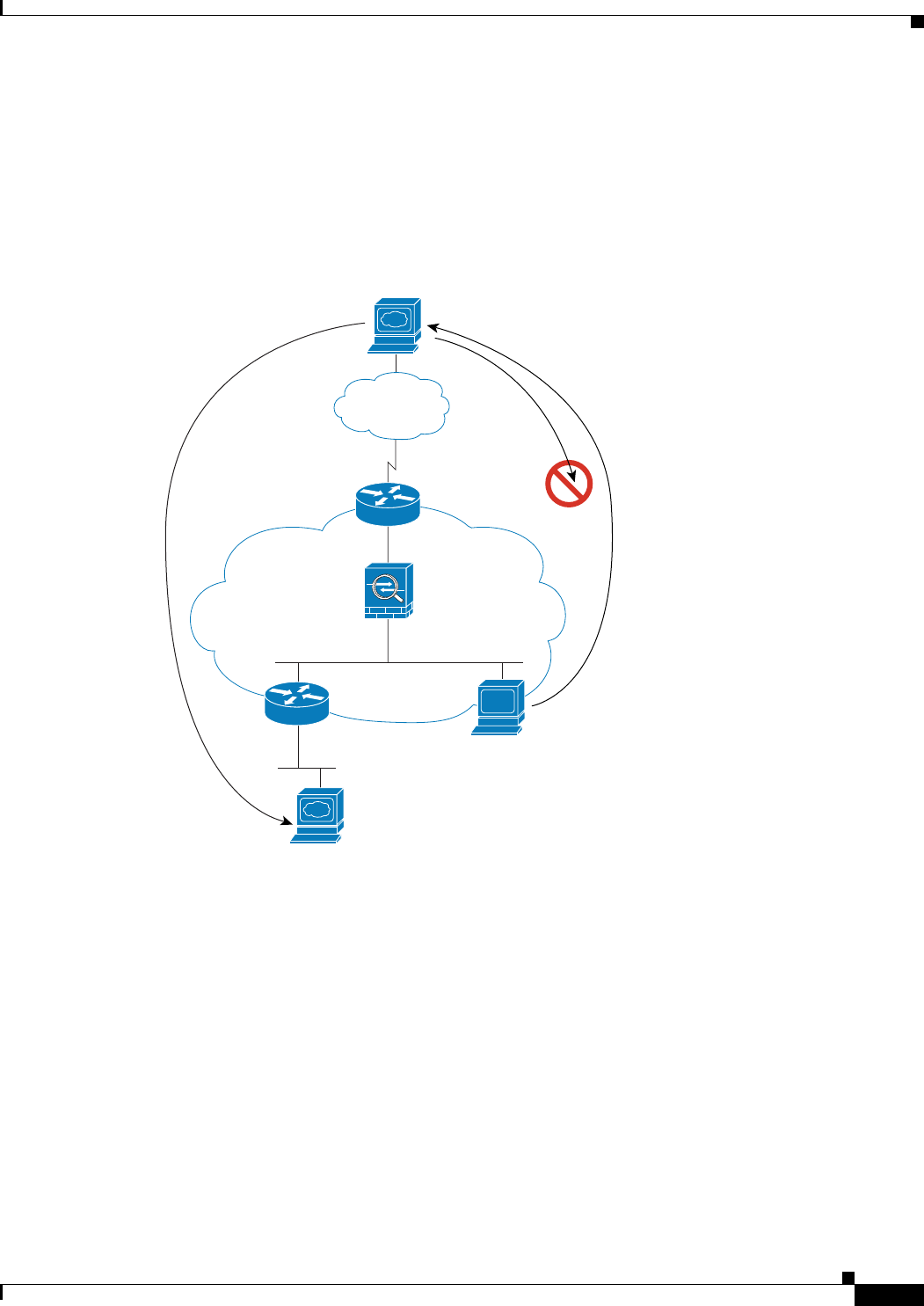
Figure 15-7 shows a typical transparent firewall implementation with an inside network that contains a
public web server. The security appliance has an access list so that the inside users can access Internet
resources. Another access list lets the outside users access only the web server on the inside network.
Figure 15-7 Typical Transparent Firewall Data Path
This section describes how data moves through the security appliance, and includes the following topics:
• An Inside User Visits a Web Server, page 15-12
• An Inside User Visits a Web Server Using NAT, page 15-13
• An Outside User Visits a Web Server on the Inside Network, page 15-14
• An Outside User Attempts to Access an Inside Host, page 15-15
www.example.com
209.165.201.2
Management IP
209.165.201.6
209.165.200.230
Web Server
209.165.200.225
Host
209.165.201.3
Internet
92412


















